Not only can the programmer not provide programming efficiency, but it has a very high rate of bad products. What is more terrible is that many bad rate chips have been damaged. Isn't this a loss for the lady and the pawn (paying for the programmer to edit the chip)?
In fact, the customer's consultation and feedback also confirm the development and change history of our programmer technology all the way, the details determine success or failure!
Usually, the use of programmers to write chips has a bad rate, which is caused by many factors, such as chip batch quality fluctuations, programming and burning room environment and personnel habits, fixture life, programmer aging, programmer timing compatibility. And so on. Solving these basic problems can generally be solved by strengthening personnel training, equipment maintenance upgrade or timely updating of the chip timing algorithm, and also achieves certain effects!
So is the problem really solved? In fact, the rate of defective products is reduced, but the phenomenon of damage to the chip still exists!
If the company invested a lot of hardware, software and timing developers to analyze the problem, but the result is that the programmer hardware design performance indicators are normal, the software does not appear abnormal BUG, ​​the algorithm timing is also strictly in accordance with the programming manual provided by the chip manufacturer. To write.
So all the focus seems to be slowly gathered in the original chip, of course, the original chip quality is excellent!

Through the unremitting efforts of the programmers and users, the original manufacturers of the chip, finally found the end of the disease.
The chip factory analyzes the failed chip feedback: the chip has two levels of encryption, the first level of chip encryption, the user can continue to repeat operations by erasing, and the second level of encryption, also known as add-on, user Once encrypted, you will not be able to do anything again! Moreover, the encryption bit is located in the Flash area of ​​the chip, occupying the first few bytes of the Flash area address;
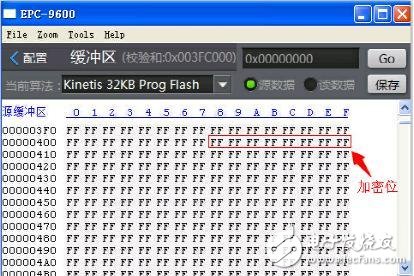
User side plan: Our program uses a second level of encryption (dead), and the encrypted information is in the programming file;
Programmer programming process: The user loads the file and performs sequential programming directly from the top to the bottom of the Flash area.
From the word "dead", we can imagine that the encryption operation of the chip must be cautious; from the above communication information, it is easy to damage the chip phenomenon, not caused by poor programming hardware, software or timing indicators. Instead, it added a deadlock to the chip and locked the chip.
The encryption bit occupies the first few bytes of the flash area of ​​the chip. If the programmer follows the normal flow operation, it writes from the flash start address of the chip to the end address. Once the chip finishes writing the encryption bit at the start address. In the subsequent tens of K, hundreds of K or even M's capacity code for a long time of burning process, there was an emergency! For example, man-made illegal operation, poor contact between the chip and the burning seat, failure to write due to the chip not responding during programming, will inevitably lead to the chip being locked and unable to be used, resulting in the chip being abolished!
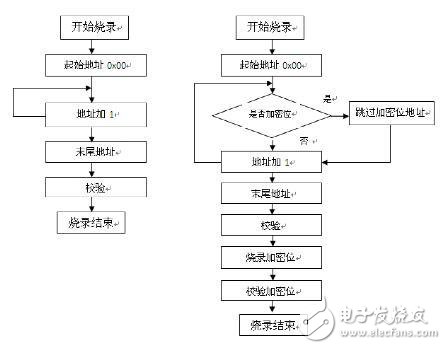
In response to this phenomenon, our programmer changed its mindset and changed the operation flow; we independently designed a "configuration". Before the programmer burns, our software will first parse and extract the encrypted bits of the user code and put them on In the "configuration"; in the process of performing the programming operation, the programmer first burns the user code except the encryption bit, and after burning successfully, finally burns the encryption bit through "configuration"; during the burning process In the case of man-made illegal operation, poor contact between the chip and the burning seat, programming failure, the chip does not respond to the burning failure, as long as the encryption bit is not operated, the chip can continue to burn, without locking The chip is damaged. This can greatly avoid damage to the chip.
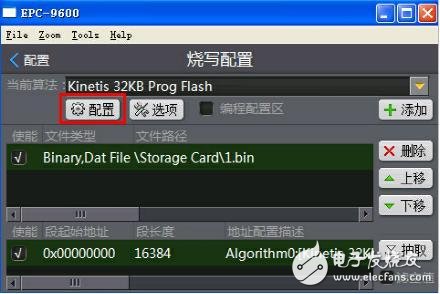
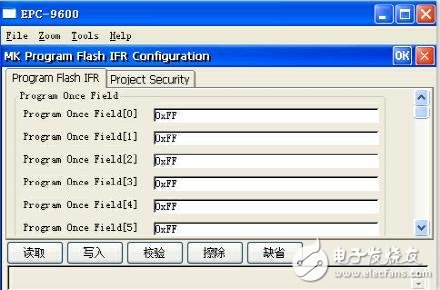
The details determine the success or failure, the programmer just changes an operation mode, change the operation sequence, you can improve the yield of chip burning, so that customers can stop programming.
·Basic precautions
Do not put expensive oil into low-quality cartridges to avoid wastage. Most pre-filled oil cartridges have the so-called 510 thread. The oil cartridge screws onto a rechargeable battery. Some of these batteries have buttons and some heat up automatically when you pump the oil. Some batteries have multiple temperature settings and some heat up to a preset temperature; these features need to be known in advance.
·Cleaning notes
Use a suitable cleaning tool to clean them, such as activated charcoal or dried tea leaves in a used pipe to absorb the oil. It is important not to use alcohol or other boiling water to clean the pipe, and to wait until it has cooled down completely before cleaning. Otherwise, the hot stem will come into contact with the watery liquid and cause the mouthpiece tenon to loosen, thus shortening the life of the 510 cartridges.
This is what you should be aware of when using 510 cartridges. At the same time, when using 510 cartridges, there are still some vaping tips, for example, when using them, be careful not to suck too hard, will not produce smoke. When you inhale too hard, the smoke is sucked directly into your mouth and not atomized by the atomizer, so gently inhaling is more powerful and gives you a better vaping experience.
510 Cartridge Oem,Leakproof 510 Cartridge,510 Battery And Cartridges Oem,510 Cartridge
Shenzhen MASON VAP Technology Co., Ltd. , https://www.cbdvapefactory.com